Setup
Bot Installation
1
Go to the Admin Dashboard
Start by opening your dashboard on the ChainPatrol app.

2
Go to Organization Settings
In the navbar, select Settings to go to your Organization Settings page.

3
Go to Integrations Tab
Once you are in the organization settings, navigate to the Integrations tab. This section contains options for the Slack bot as well as other integrations.

4
Complete Slack OAuth
In the Integrations tab, you will find an option to Add to Slack. Click this button, then you will be redirected to the Slack authorization page. Click Allow.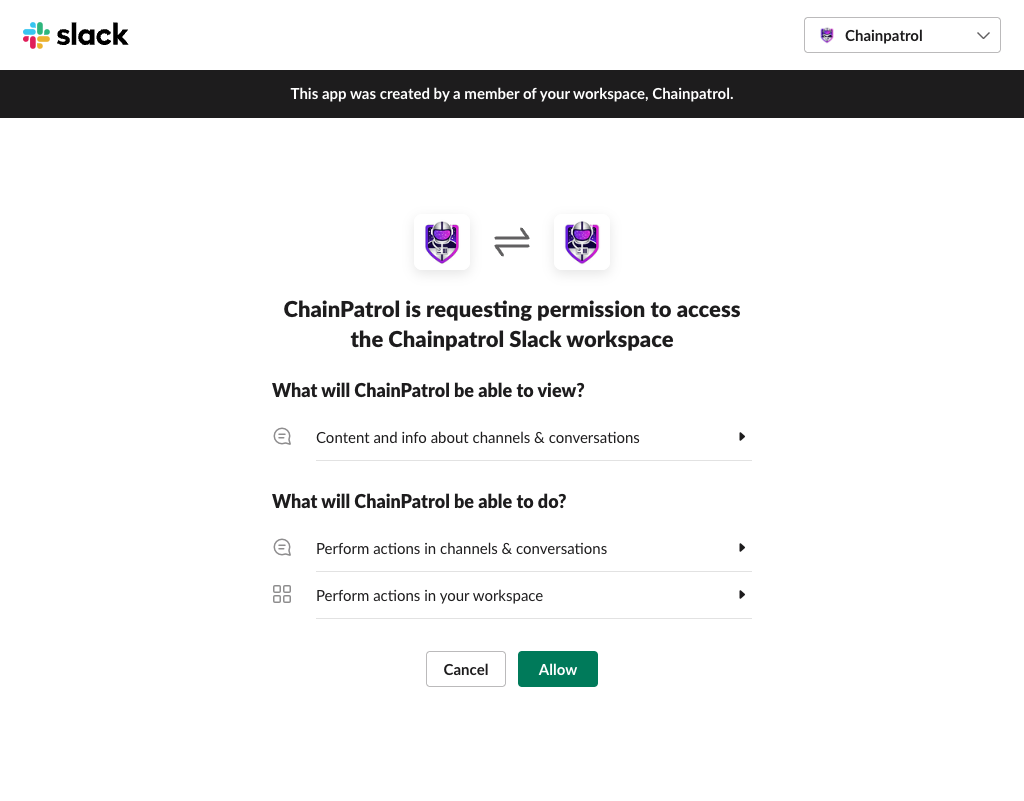

Confirmation and Finalization
The ChainPatrol Slack Bot should appear in your listed apps along with other allowed workspace apps.
Adding ChainPatrol Bot To Your Reporting Channel
Channel You Want To Take Report From
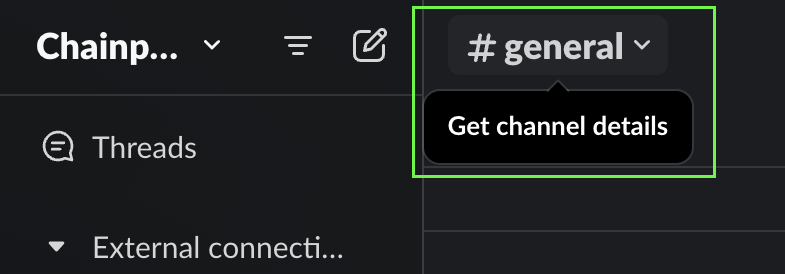
Integrations
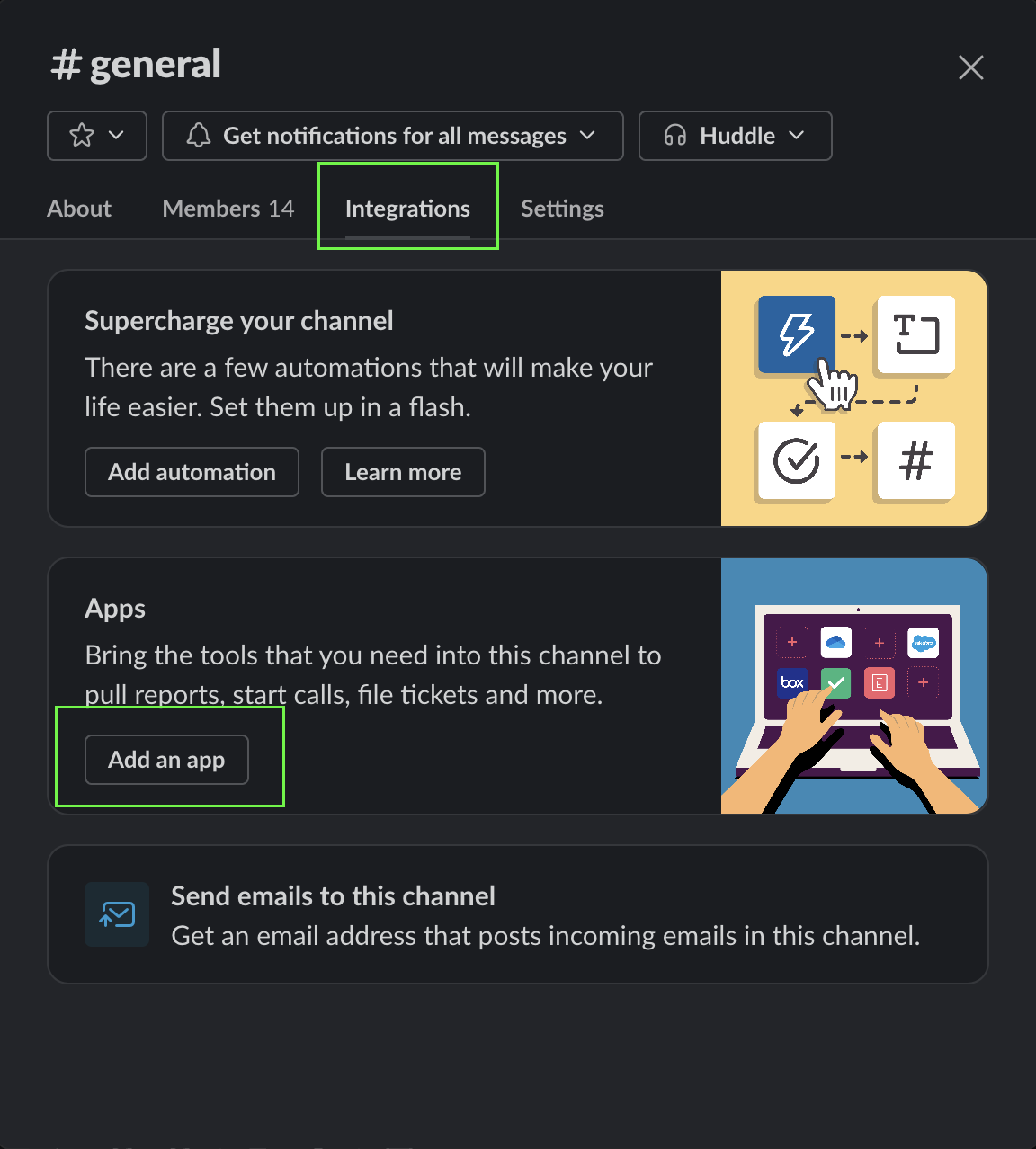
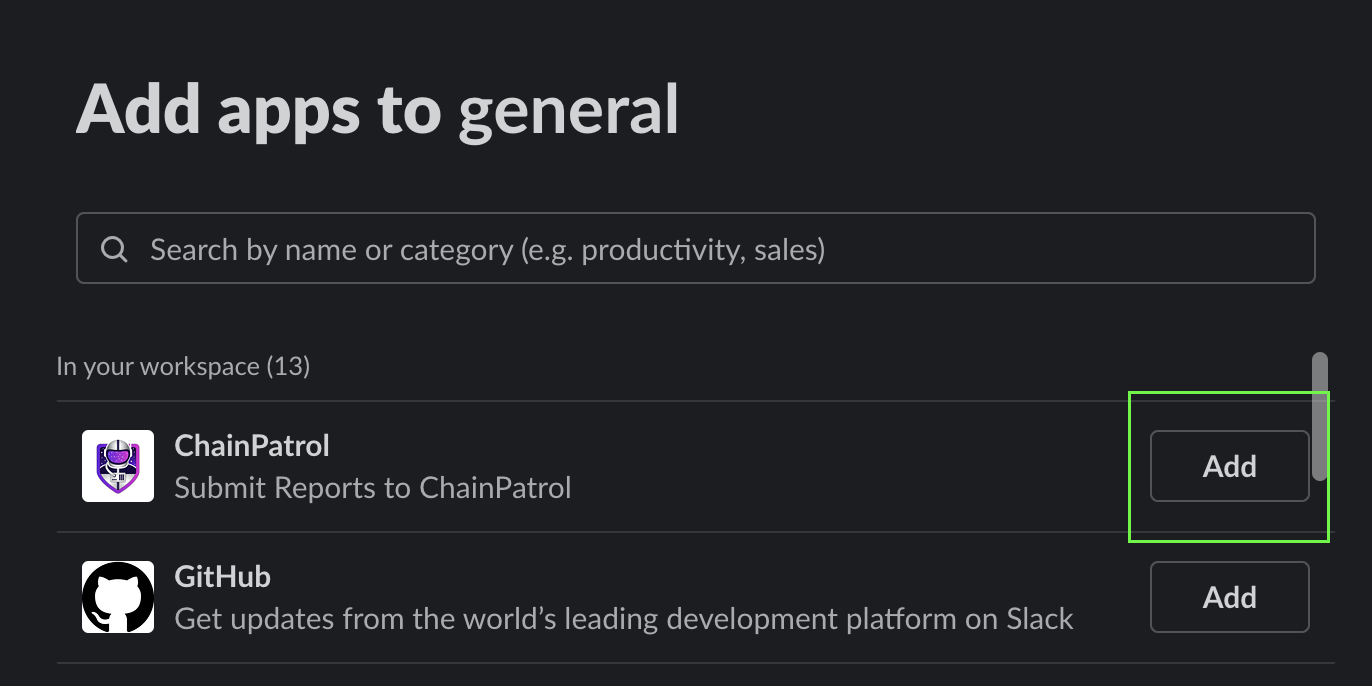
Add ChainPatrol
Link Organization
Please send ChainPatrol staff your workspace’s Slack Team ID so that we can finish the automated pipeline.- Follow Slack’s documentation to locate your Team ID.
Usage
Once the bot is added to your workspace and you have sent ChainPatrol your Team ID, you can use the following actions:Slash Commands
/chainpatrol <url>- Submit a scam report for the given URL
Shortcut Actions
For a given message, click on the kebab menu and then select theCreate Report option.
Kebab Menu
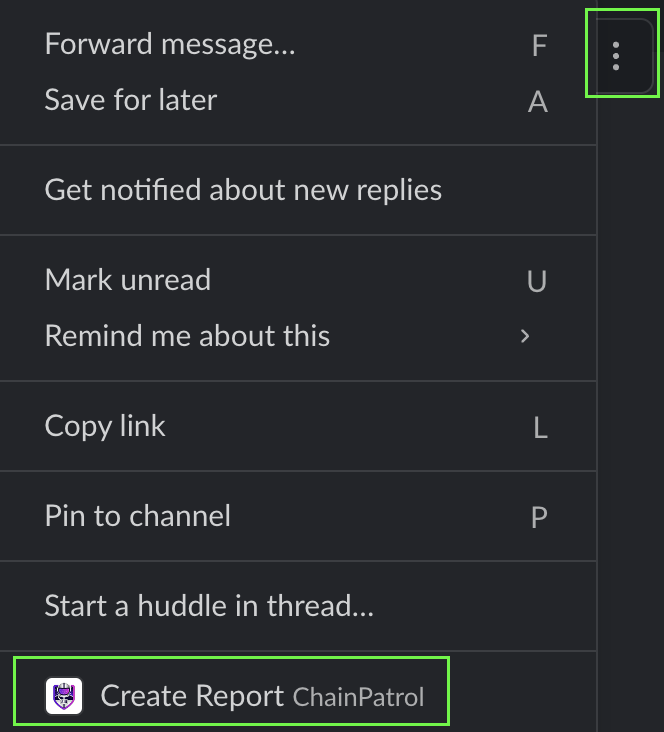
Report Modal
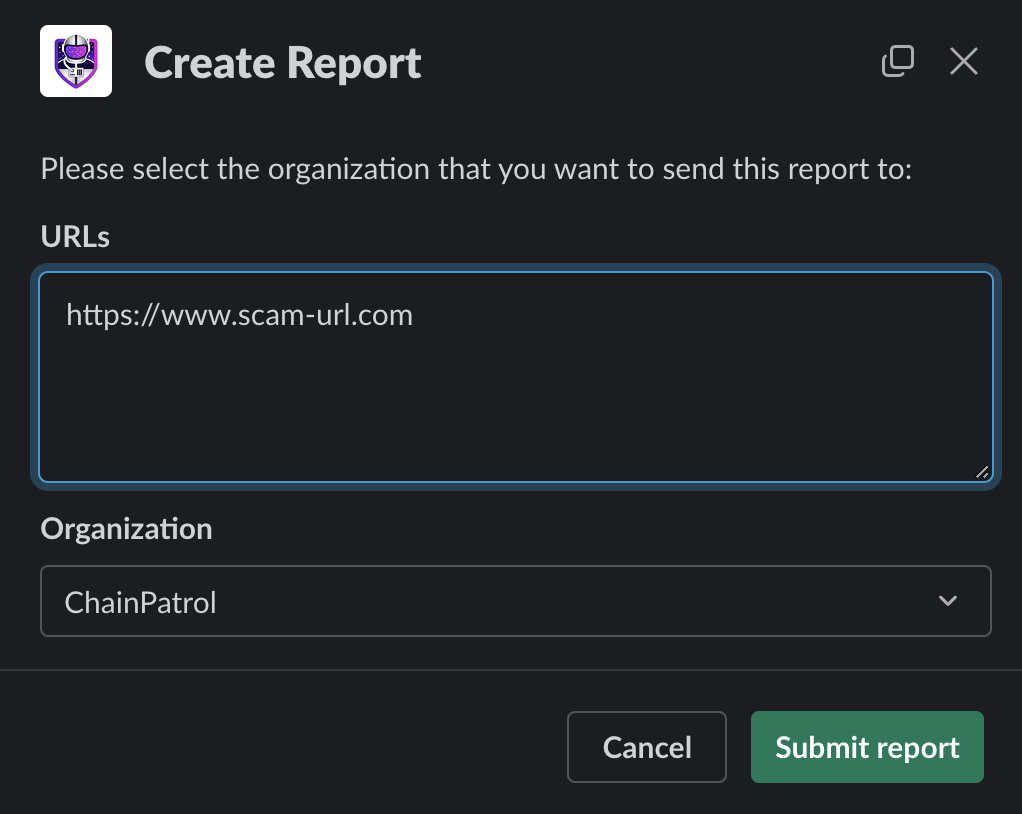
Threats Feed Configuration
In addition to submitting reports, the ChainPatrol Slack Bot can also send automated notifications about threats and reports to your Slack channels. This creates a real-time threats feed that keeps your team informed about security activity.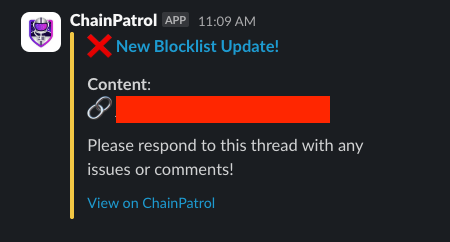
Setting Up Notification Settings
1
Create and Configure Notification Channel
Create a dedicated channel in your Slack workspace for receiving ChainPatrol threat notifications. This channel will serve as your organization’s security feed for real-time threat intelligence.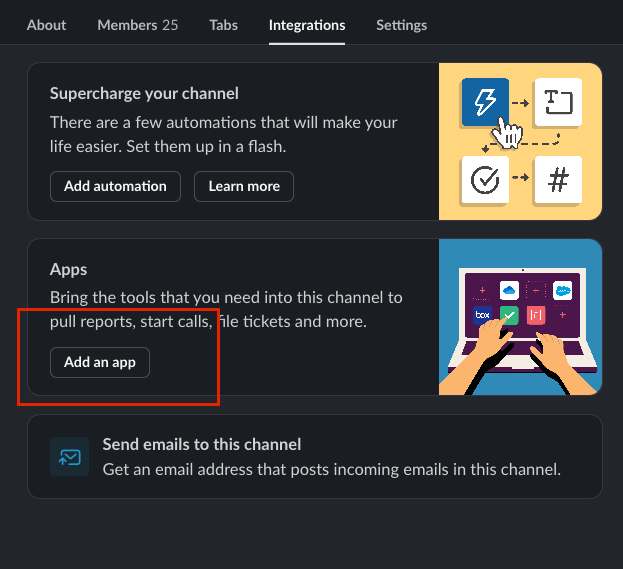

2
Provide Channel Information to ChainPatrol
Contact ChainPatrol staff with your notification channel’s Channel ID to complete the integration setup. The Channel ID is a unique identifier that begins with “C” and can be found in your channel’s details.
3
Access Integration Settings
Navigate to your ChainPatrol dashboard and go to Settings > Integrations to configure your notification preferences.
4
Configure Notification Preferences
Within the Integrations tab, locate the Notification Settings section to customize which types of security alerts your team receives.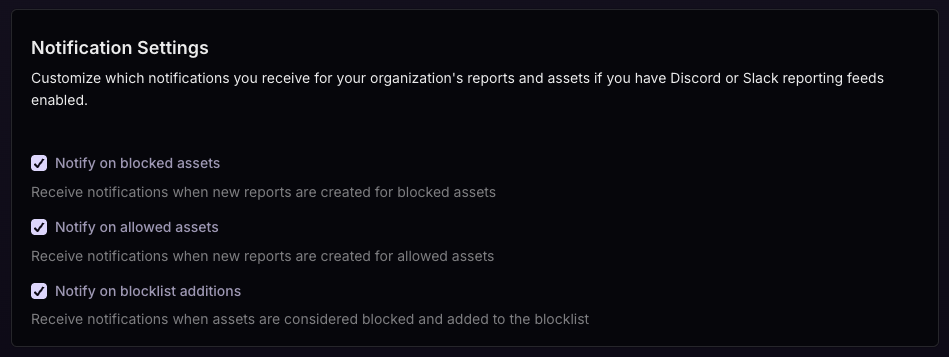

5
Select Notification Types
Choose which notifications you want to receive for your organization’s reports and monitored assets. Each option serves different security monitoring needs as detailed below.
Notification Options
New Reports for Blocked Assets
Receive notifications when new reports are created for assets that are
already on your blocklist. This helps you track ongoing threats and see when
community members are encountering known malicious content.
New Reports for Allowed Assets
Receive notifications when new reports are created for assets that are
currently on your allowlist. This can help identify potential false
positives or assets that may need review if they’re receiving multiple
reports.
Assets Added to Blocklist
Receive notifications when assets are confirmed as threats and added to the
blocklist. This is the most critical notification type - when you see
this alert, it means ChainPatrol’s systems have confirmed a threat and are
actively working to process it for takedown and blocklist distribution.